Change SSH Port from 22 to Custom Port
Complete Security Hardening Guide with Firewall Configuration & Recovery Options
- AlmaLinux: 8.x through 9.6 (including all minor versions)
- Rocky Linux: 8.x and 9.x
- CentOS: 7.x, 8.x (Stream)
- RHEL: 7.x, 8.x, 9.x
- Ubuntu: 18.04 LTS, 20.04 LTS, 22.04 LTS, 24.04 LTS
- Debian: 10 (Buster), 11 (Bullseye), 12 (Bookworm)
- CloudLinux: 7.x, 8.x, 9.x
- Oracle Linux: 7.x, 8.x, 9.x
Note: Commands may vary slightly for systemd vs init.d systems. This guide uses systemd commands which work on all modern distributions listed above.
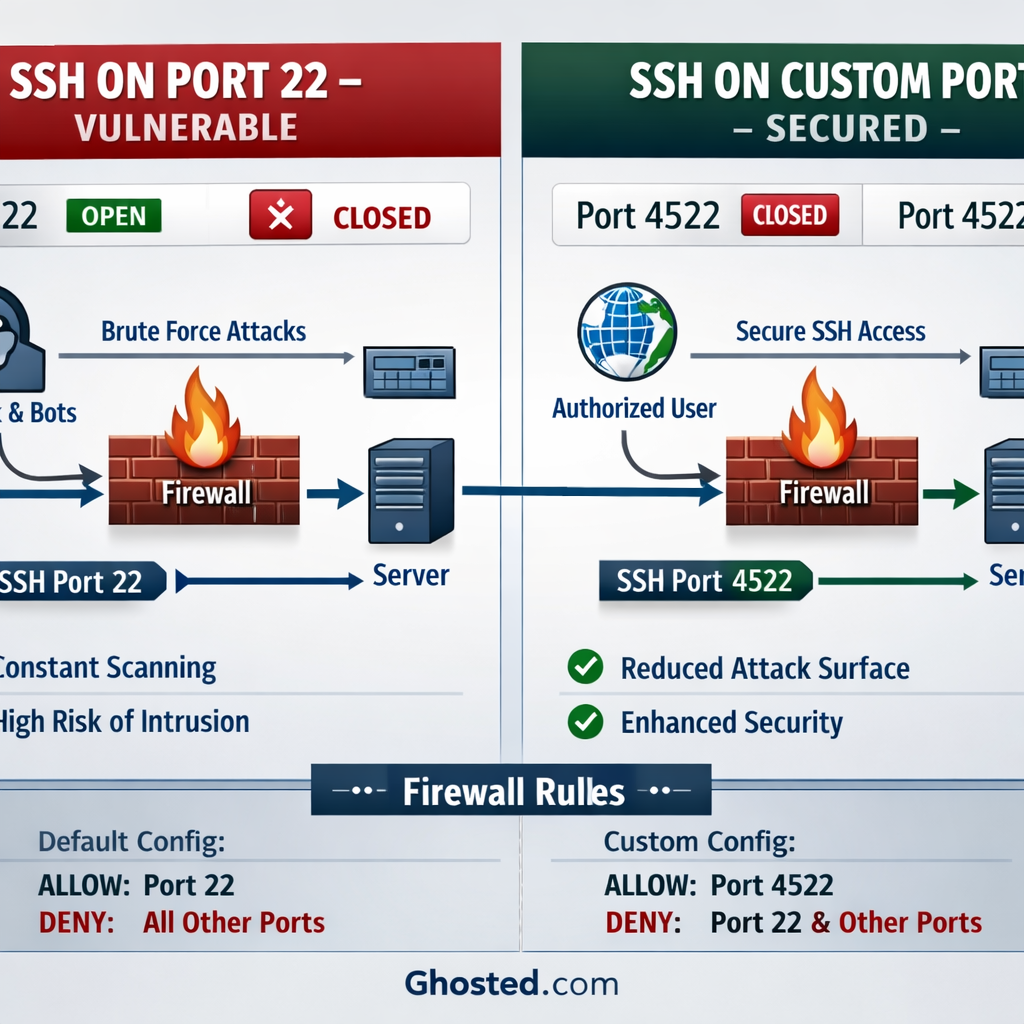
🛡️ Why Change Your SSH Port from 22?
Port 22 is the default SSH port that every hacker and automated bot knows. Changing it provides immediate security benefits:
- 90-95% Reduction in Automated Attacks: Bots constantly scan port 22 on every server
- Cleaner Security Logs: Distinguish real threats from automated noise
- Reduced Server Load: Less CPU wasted on processing fake login attempts
- Defense in Depth: Additional security layer alongside strong passwords and key authentication
- Compliance Benefits: Many security standards recommend non-standard ports
📌 Recommended Custom Port Ranges
Popular secure port choices:
2222– Easy to remember (used in this guide)2200-2300– Common alternate SSH range8022– Another memorable option10000-10100– High port range20000-30000– Very high range, less commonly scanned
Note: You can use any port between 1024-65535. Avoid ports below 1024 (privileged) and common service ports. Throughout this guide, we’ll use port 2222 as an example – replace it with your chosen port.
Always create a backup before making critical changes. This allows easy restoration if needed:
This creates a timestamped backup file for easy identification.
Edit CSF configuration to allow your custom port (we’re using 2222):
Find the TCP_IN line and add your custom port. Change from:
To (adding 2222 or your chosen port):
Save with Ctrl+O, then exit with Ctrl+X
Apply the CSF changes:
Add your custom SSH port to Imunify360’s whitelist:
Verify the port was whitelisted:
For iptables:
For UFW (Ubuntu/Debian):
Now edit the SSH daemon configuration file:
Find the line (usually near the top):
Change it to your custom port (remove the # to uncomment):
Port 22Port 2222This allows you to test the new port while keeping the old one active. Remove port 22 after confirming the new port works.
Save with Ctrl+O, then exit with Ctrl+X
Test the SSH configuration file for syntax errors before restarting:
❌ If you see errors: Review your changes in step 5
Also verify SELinux permissions (if SELinux is enabled):
Restart the SSH daemon to apply changes:
Check that SSH is running properly:
Verify SSH is listening on the new port:
You should see SSH listening on port 2222 (or your chosen port)
In a NEW terminal window, test connecting with the custom port:
For servers with hostnames:
❌ Connection Failed? Don’t panic! See the recovery section below
🚨 SSH Connection Failed? Recovery Options
Don’t panic! Your original session is still active. Here are recovery methods:
Option 1: Use cPanel Terminal (Recommended)
- Log into cPanel at:
https://your-server:2083 - Navigate to Advanced → Terminal
- Switch to root:
sudo su -orsu - - Edit SSH config:
nano /etc/ssh/sshd_config - Change port back to 22 and restart:
systemctl restart sshd
Option 2: Use WHM Terminal
- Log into WHM at:
https://your-server:2087 - Navigate to System → Terminal
- Fix the SSH configuration as root
Option 3: VNC/Console Access
- Use your hosting provider’s VNC or console access
- Most providers offer this in their control panel
- Works even if SSH is completely broken
Common Issues to Check:
- Firewall blocking: Ensure the port is open in ALL firewalls
- Typo in port number: Verify you’re using the same port everywhere
- SELinux blocking: Check SELinux permissions
- SSH syntax error: Run
sshd -tto check
Step 1: Remove port 22 from SSH config
Remove or comment out the Port 22 line, keeping only:
Step 2: Restart SSH
Step 3: Remove port 22 from CSF (if using CSF)
Remove 22 from the TCP_IN line, then restart CSF:
Step 4: Update other firewalls accordingly
Remove port 22 rules from iptables, firewalld, or UFW as needed.
Update SSH client configurations:
For command line SSH: Add to ~/.ssh/config:
For PuTTY (Windows):
- Update saved sessions with the new port
- Change port from 22 to 2222 in connection settings
For FileZilla/SFTP clients:
- Update site manager entries
- Change port to 2222 for SFTP connections
- Document the port change in your server notes
- Inform your team members about the new port
- Update any monitoring systems or scripts
- Update backup scripts that use SSH/SFTP
- Save the connection details securely
New connection command:
ssh -p 2222 username@your-serverSecurity improvements achieved:
• 90-95% reduction in automated SSH attacks
• Cleaner security logs for better threat detection
• Reduced server load from bot attempts
• Additional layer of security (defense in depth)
• Better compliance with security best practices
• Enable SSH key authentication and disable passwords
• Install Fail2Ban for intrusion prevention
• Limit SSH access to specific IP addresses
• Use strong, unique passwords if password auth is needed
• Regularly review SSH logs:
/var/log/secure or /var/log/auth.log• Keep your backup:
/etc/ssh/sshd_config.backup-*
Need Professional Server Security Management?
Changing your SSH port is just one step in comprehensive server security. Contact Ghosted.com for professional server hardening, security audits, and managed hosting solutions. Our experts ensure your servers are protected with industry-leading security practices while maintaining optimal performance.
We offer complete security packages including firewall configuration, intrusion detection, DDoS protection, and 24/7 monitoring.
🌟 About Ghosted.com Security Solutions
Ghosted.com specializes in enterprise-grade server security and managed hosting solutions. Our team of security experts ensures your infrastructure remains protected against evolving threats.
Security Hardening
Complete server security audits and hardening services
Managed Firewalls
CSF, Imunify360, and custom firewall configurations
24/7 Monitoring
Real-time threat detection and incident response
Secure Hosting
Pre-hardened servers with advanced security features
Whether you need help securing your current servers or want fully managed secure hosting, our team is ready to protect your digital assets with proven security strategies.
Get Started with Ghosted.com Security Services© 2025 Ghosted.com – Enterprise Security & Hosting Solutions